WireGuard Basics
WireGuard is a very easy to understand and modern VPN solution. It aims to be faster, simpler and leaner than IPsec. It also wants to deliver mre performance than OpenVPN. In contrast to OpenVPN, it uses a reduced number of (state-of-the-art) cryptographic methods. WireGuard is designed as a universal VPN for operation on embedded devices and supercomputers. This article shows the components and functionality of WireGuard.
Development and current status
WireGuard was created by Jason A. Donenfeld, also known as "zx2c4". The first release 0.0.20161209 was released on December 09, 2016.[1] WireGuard is still undergoing a lot of further development, so the developers warned against using the code until 24.08.2019:[2]
- WireGuard is not yet complete. You should not rely on this code. It has not undergone proper degrees of security auditing and the protocol is still subject to change. We're working toward a stable 1.0 release, but that time has not yet come.[...]
The developers have been writing since 28.08.2019:[3]
- WireGuard is currently working toward a stable 1.0 release. Current snapshots are generally versioned "0.0.YYYYMMDD" or "0.0.V", but these should not be considered real releases and they may contain security quirks (which would not be eligible for CVEs, since this is pre-release snapshot software). This text will be removed after a thorough audit.
Despite being declared as incomplete and not yet stable, WireGuard is already being promoted by the developers as the most secure, easiest to deploy and simplest VPN technology on the market.
The development can be tracked in the WireGuard Git repository:
- index : WireGuard (git.zx2c4.com)
Availability
Originally WireGuard was released for the Linux kernel, at least kernel 3.10 is required for installation.[4]
Now WireGuard is available for FreeBSD, Linux, macOS, OpenBSD, Windows and other operating systems as well as an app for Android and iOS.[5]
Advantages of WireGuard
The advantages of WireGuard are:
- Quick and easy setup
- Slim code base
- Focus on a few but modern cryptographic techniques
- Supports many operating system variants
- Switch between WLAN and mobile connection without noticeable interruption
- Very fast connection setup
- Very high speed
- Open Source
Disadvantages of WireGuard
WireGuard has restrictions for VPN application purposes in the area of anonymization:[6]
- Cannot be used without logging.
- No dynamic IP assignment, each client has a fixed IP.
How it works
This section explains how WireGuard works, then explains how to encrypt and decrypt packets using an example process:
- WireGuard uses UDP to transmit the encrypted IP packets.
- The port can be freely selected from the high ports range.
- If no port is specified, WireGuard starts at 51820/UDP.
- Cryptokey Routing[7]
- The Public Keys are combined with a list of Allowed IPs.
- If the association is successful, the packets are allowed to pass through the VPN tunnel.
- Properties of Public-Keys
- Each peer has its own private and public key.
- Used to authenticate the peers to each other.
- Have a similar functional principle to SSH Public-Keys.
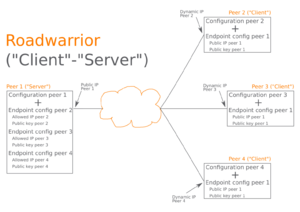
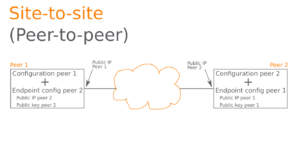
- Typical WireGuard server configuration
- A single entry for an interface is created.
- Several peers are associated with this one interface.
- Clients, e.g. road warrior devices, often have only one interface entry and one peer (the WireGuard "Server").
- Traffic Routing via AllowedIPs
- Wildcard 0.0.0.0/0: This automatically encrypts any packet and sends it through the VPN tunnel.
- (Multiple) specification of IP addresses or network addresses with subnet mask, separated by comma: The traffic is only sent through the tunnel for the specified IP addresses.
- Properties of the Allowed IPs list
- In sending direction this list behaves like a routing table.
- In receiving direction it serves as Access Control List.
Encryption of a packet
A packet is to be sent to the IP address 192.168.1.10. WireGuard checks which peer this IP corresponds to. If the peer associated with the IP address cannot be found, the packet is discarded. If the peer can be assigned successfully, it is encrypted with its public key (e.g. public key of the peer "Ubuntu Client 2"). WireGuard then checks which public endpoint the client "Ubuntu Client 2" has. The associated endpoint for this client is "8.8.8.8:51820" and now the encrypted packet is forwarded to this endpoint.
Decryption of a packet
When a WireGuard peer receives a packet, it is then decrypted (using its own private key). If it has been successfully decrypted and authenticated for a known peer (e.g. "Ubuntu Client 1"), it will then check what the last known public endpoint for that peer was (4.4.4.4:51820). The decrypted packet contains the plaintext packet from the IP address 192.168.1.9. Now it is checked if the peer "Ubuntu Client 1" is allowed to send packets from the IP 192.168.1.9 to this peer. If the check is successful, the packet will be accepted. If not, the packet is discarded.
Examples
In our Thomas-Krenn-Wiki you will find detailed installation instructions for WireGuard:
- OPNsense WireGuard VPN for Road Warrior configuration
- Ubuntu 18.04 as WireGuard VPN client configuration
References
- ↑ Snapshot 20161209 (git.zx2c3.com)
- ↑ Work in Progress (web.archive.org - wireguard.com) Stand 24.08.2019
- ↑ Work in Progress (web.archive.org - wireguard.com) Stand 28.08.2019
- ↑ Kernel Requirements (wireguard.com)
- ↑ Installation (wireguard.com)
- ↑ WireGuard VPN: What You Need to Know (restoreprivacy.com, 28.06.2019)
- ↑ Cryptokey Routing (wireguard.com)
|
Author: Thomas Niedermeier Thomas Niedermeier working in the product management team at Thomas-Krenn, completed his bachelor's degree in business informatics at the Deggendorf University of Applied Sciences. Since 2013 Thomas is employed at Thomas-Krenn and takes care of OPNsense firewalls, the Thomas-Krenn-Wiki and firmware security updates.
|