OPNsense OpenVPN performance tests and results
The free firewall solution OPNsense offers various options for configuring a VPN connection. By default OPNsense supports IPsec and OpenVPN connections. These techniques can be used, among other things, for the static connection of two sites via a site-to-site connection. The choice of encryption technique depends strongly on the required throughput. This article shows the results of the OpenVPN performance tests with iperf we determined when using a Site-to-Site connection. The VPN performance was also tested with IPsec. You can find detailed results in the Wiki article OPNsense IPsec performance tests.
Test setup
The test setup for these tests consists of two OPNsense firewall systems with one client system each on the LAN side. The two firewalls are connected to a switch with the respective WAN interface. The current OPNsense version was used on both firewalls at the time of the test. On the client systems the current Ubuntu Server LTS was used at the time of the test. Further details and a detailed list can be found in the sections with the test results.
Test settings
This section lists the components used, the parameters used and the test procedure.
Test software
For the speed tests the tool iperf version 2.0.10 was used on the clients.
$ iperf -v iperf version 2.0.10 (2 June 2018) pthreads
Test parameter
All tests were performed with the following parameters:
- Server: iperf -p 5000 -f m -s
- Client: iperf -p 5000 -f m -c <IP-des-Servers> -t 180 -P 10
Test procedure
Iperf was started in server mode on Client 1 of Site 1. Then iperf was started in client mode on the client side. This made it possible to determine the upload speed from the client side to the server side. To measure the download performance, the server side and client side were swapped. 10 upload and 10 download tests were performed. The values were added and the mean value was calculated. The same applies to the measured load of the systems.
OpenVPN settings
The following settings were used in the test:
- Server Mode: Peer to Peer (SSL/TLS)
- Protocol: UDP
- TLS Authentication: 2048 bit
- DH Parameters Length: 4096 bit
- Encryption algorithm: AES-128-GCM
- Auth Digest Algorithm: SHA256 (256-bit)
Test results OpenVPN with TLS
The following sections break down the results according to the firewall devices used and tabulate the results. The server mode of OpenVPN has been set to Peer to Peer (SSL/TLS), because in contrast to a pre-shared key configuration an AES GCM based encryption can be used.[1]
Setup with Supermicro X11SSH-LN4F and Thomas-Krenn LES compact 4L
The following table shows the components of the test with the Supermicro X11SSH-LN4F and Thomas-Krenn LES compact 4L:
| Application purpose | Hardware | BIOS informations | Software |
|---|---|---|---|
| Firewall Site 1 |
|
|
|
| Firewall Site 2 |
|
| |
| Client Site 1 |
|
|
|
| Client Site 2 |
|
|
Test results Thomas-Krenn LES compact 4L
In this table you will find the values determined by us during the tests of an OpenVPN site-to-site connection with Firewall 1 (Supermicro X11SSH-LN4F and Firewall 2 (Thomas-Krenn LES compact 4L). Tests with Hyper-Threading enabled were not performed because the CPU of the LES compact 4L does not support this. All measurement results were determined from the mean value of 10 passes.
| Test without Hyper-Threading | Throughput download on LES
LES compact 4L: decrypts X11SSH-LN4F: encrypts |
Throughput upload on LES
LES compact 4L: encrypts X11SSH-LN4F: decrypts |
|---|---|---|
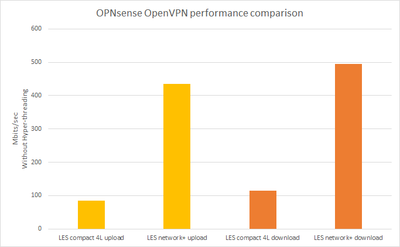
| Throughput | 114,9 Mbits/sec | 84,74 Mbits/sec |
| Load on LES compact 4L
(vmstat -w 180 -c 2) |
us - sy - id
9 - 23,9 - 67,4 |
us - sy - id
9 - 23,9 - 67,2 |
| Load on X11SSH-LN4F
(vmstat -w 180 -c 2) |
us - sy - id
1,8 - 4 - 95 |
us - sy - id
1,6 - 3 - 95 |
The results of the individual test rounds are summarized in a zip archive.
Setup with Supermicro X11SSH-LN4F and Thomas-Krenn LES network+
The following table shows the components of the test with the Supermicro X11SSH-LN4F and Thomas-Krenn LES network+:
| Application purpose | Hardware | BIOS informations | Software |
|---|---|---|---|
| Firewall Site 1 |
|
|
|
| Firewall Site 3 |
|
| |
| Client Site 1 |
|
|
|
| Client Site 3 |
|
|
Test results Thomas-Krenn LES network+
The following section shows the values determined by us during the tests of an OpenVPN site-to-site connection with Firewall 1 (Supermicro X11SSH-LN4F and Firewall 3 (Thomas-Krenn LES network+). Note: In this test setup, the tests were performed with Hyper-Threading activated on both firewalls and deactivated on both sides.
All measurement results were determined from the mean value of 10 passes:
| Test without Hyper-Threading | Throughput download on LES
LES network+: decrypts X11SSH-LN4F: encrypts |
Throughput upload on LES
LES network+: encrypts X11SSH-LN4F: decrypts |
|---|---|---|
| Throughput | 495 Mbits/sec | 435,3 Mbits/sec |
| Load on LES network+
(vmstat -w 180 -c 2) |
us - sy - id
17,7 - 41,1 - 41,3 |
us - sy - id
17 - 42,3 - 40,6 |
| Load on X11SSH-LN4F
(vmstat -w 180 -c 2) |
us - sy - id
5 - 13 - 82 |
us - sy - id
4 - 11,5 - 84 |
| Test with Hyper-Threading | Throughput download on LES
LES network+: decrypts X11SSH-LN4F: encrypts |
Throughput upload on LES
LES network+: encrypts X11SSH-LN4F: decrypts |
|---|---|---|
| Throughput | 466,5 Mbits/sec | 394,3 Mbits/sec |
| Load on LES compact 4L
(vmstat -w 180 -c 2) |
us - sy - id
11 - 19,5 - 69,9 |
us - sy - id
10,8 - 20,1 - 69,2 |
| Load on X11SSH-LN4F
(vmstat -w 180 -c 2) |
us - sy - id
3 - 6 - 91 |
us - sy - id
3 - 5,8 - 91,9 |
The results of the individual test rounds are summarized in a zip archive.
Findings of the tests
The results of the tests with OpenVPN can be summarized with the following points:
- Performance significantly lower than with an IPsec connection.
- OpenVPN runs only single-threaded, does not benefit from multi-core CPUs.
- More configuration options.
References
- ↑ Setup SSL VPN site to site tunnel (docs.opnsense.org)
|
Author: Thomas Niedermeier Thomas Niedermeier working in the product management team at Thomas-Krenn, completed his bachelor's degree in business informatics at the Deggendorf University of Applied Sciences. Since 2013 Thomas is employed at Thomas-Krenn and takes care of OPNsense firewalls, the Thomas-Krenn-Wiki and firmware security updates.
|