Security Recommendations for Remote Maintenance Features for IPMI Chips with ATEN-Software
On October 21 2011, we were notified about three security problems in the remote maintenance features for Supermicro systems using the Nuvoton WPCM450R IPMI Chips with ATEN-Software.
In this wiki article, you can find information about these security problems and recommendations for their resolution.
Update - see also:
- Libupnp Buffer Overflow in Motherboards with Nuvoton Chips with IPMI WPCM450R Software (June 2013)
- Supermicro IPMI Security Updates November 2013 (November 2013)
General Security Information
We recommend not operating administrative access interfaces, such as IPMI and those similar to SSH services, openly on the Internet, but only making access to them available to authorized personnel by means of firewalls and VPNs. This recommendation is valid regardless of the security problems described here.
In addition to protection by a dedicated firewall, the X9-series motherboards provide an integrated firewall for remote maintenance features (see Integrated IPMI Firewall Supermicro X9 Motherboards).
Affected Hardware
Servers with motherboard including Nuvoton WPCM450R IPMI Chips with ATEN-Software are affected.
The motherboards from the Thomas Krenn catalog are:
- Main boards for Intel CPUs:
- Main boards for AMD CPUs:
Security Problem 1: Default Password for Anonymous Users
Default password for anonymous users:[1][2]
- In addition to the ADMIN account, there is a second standard user who is displayed with the Anonymous user name in the IPMI web interface.
- This Anonymous user has the password, admin.
- On many systems, this Anonymous user has administrator rights. In the newest versions of the firmware, the rights have set, in part, to No Access (displayed in the web interface as Reserved).
- Access is not truly possible using the Anonymous user name, however, when a user name is not entered, the following systems can be accessed:
- SSH access to the SMASH CLP feature
- Access to the web interface, when the Javascript inquiry for monitoring the user name has been removed (such as by saving the HTML code, removing the Javascript inquiry and replacing the relative link in the HTML source code with absolute link that contain the IP address of the IPMI interface)[3]
Suggestion for Resolution
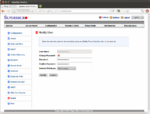
- Set a secure password for the Anonymous user and set their rights to No access (see picture, right).
- The Anonymous rights are set to No access by default for new versions of the firmware versions (see Security Problem 2).
Security Problem 2: Unprotected IPMI Configuration File
Unprotected IPMI configuration file:[4]
- The file with the IPMI configuration parameters can be accessed through http://IP-OF-IPMI/save_config.bin without user authentication after the Save IPMI Configuration has been used.
- The save_config.bin file is a .tar.gz archive. The ps.xml file contained in the archive contains the user passwords in plain text.
Suggestion for Resolution
- The problem has been corrected by the following IPMI firmware updates (the power must be cycled after the update so that the fixes take effect).
- Problem resolution options for older versions of the firmware:
- As long as the Save IPMI Configuration feature has not yet been used, the http://IP-OF-IPMI/save_config file will not exist. Do not use this feature unless absolutely necessary.
- In the event that you do need the feature or have already used it, change the password for the IPMI user.
Security Problem 3: Unprotected Screenshot
Unprotected screenshot:[5]
- The last screen that was created from "System" -> "System Information" can be accessed without authentication from http://IP-OF-IPMI/images/Snapshot.bmp.
Suggestion for Resolution
The problem has been corrected by the following IPMI firmware updates (the power must be cycled after the update so that the fixes take effect).
- Main boards for Intel CPUs:
- X9SCM-F--> Firmware from 1.45
- X8DTL-3F --> Firmware from 2.44
- X7SPE-HF-D525 and X7SPE-HF / X7SPA-HF --> Firmware from 2.66
- X8SIL-F --> Firmware from 2.66
- Main boards for AMD CPUs:
- Problem resolution options for other main boards
- Please note that this screenshot does not contain any information critical to security.
References
- ↑ Supermicro IPMI documentation omission: presence of second admin account (Full disclosure mailing list, 12.10.2011)
- ↑ SuperMicro IPMI Security (webhostingtalk.com, 09.11.2010)
- ↑ Supermicro IPMI documentation omission: presence of second admin account (Reply) (Full disclosure mailing list, 15.10.2011)
- ↑ Supermicro IPMI: backup function causes password to be stored at public web location (Full disclosure mailing list, 11.10.2011)
- ↑ Supermicro IPMI: backup function causes password to be stored at public web location (Reply) (Full disclosure mailing list, 12.10.2011)